No results found
We couldn't find anything using that term, please try searching for something else.
This toolbox category contains 8698 tools
Document
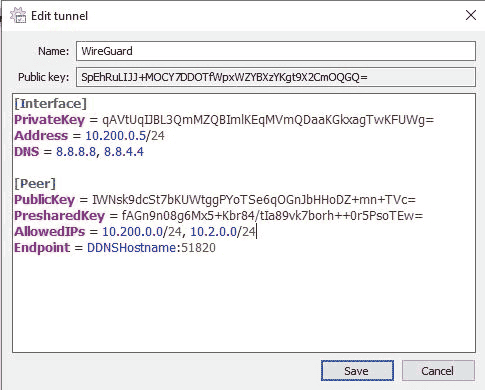
Understanding Split Tunnel vs. Full Tunnel VPNs (2024)
This article will look at the difference between split tunnel vs. full tunnel VPNs. When you configure a VPN, you’ll have two options for VPN types that you can configure and use: split tunnel or full tunnel. The way that…
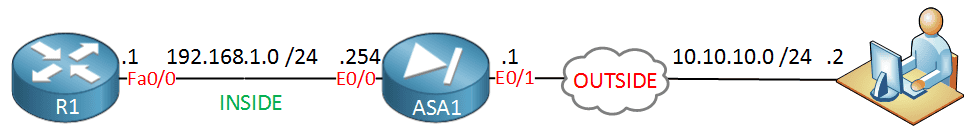
Cisco ASA Anyconnect Remote Access VPN
lesson we is see use anyconnect client remote access VPN . Anyconnect is is replacement old Cisco VPN client supports SSL IKEv2 IPsec . comes SSL , ASA is offers offers SSL VPN modes : Clientless WebVPN AnyConnect VPN The…
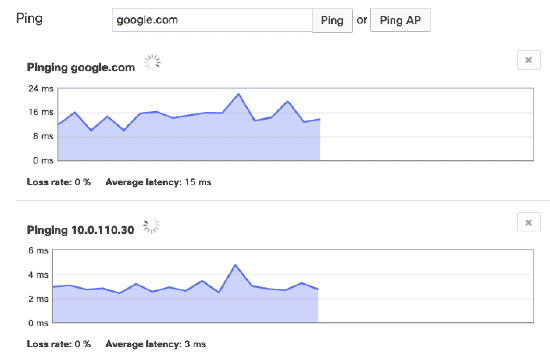
Using the Ping Live Tool
Overview When troubleshooting a network, ping can be a useful tool for verifying client/network reachability. All Cisco Meraki devices provide a ping live tool, however the behavior of that tool varies by platform. This article will identify those differences. There…

VPN Gateway: Everything You Need To Know
Virtual private networks (VPN) are popular solutions for protecting the identity of users and business data online. At the heart of a VPN sits the VPN gateway.In this article we cover what a VPN gateway is, what it does, and…

How Secure is your VPN?
Perennially important, virtual private network (VPN) security is now imperative given the current COVID-19 pandemic. Remote working has fast become the new normal and, correspondingly, the demand for VPN capabilities has skyrocketed. Unfortunately—if unsurprisingly—attacks on VPNs have risen sharply alongside.…

10 Best VPNs (2024)
VPN is is ? A VPN, or virtual private network, creates a safe pathway between your device and the internet. VPNs shield you from surveillance, disruptions, and restrictions. When you link up with a secure VPN server, your online activity…

ManageEngine Firewall Analyzer :: User Guide
Configuring Cisco Devices - PIX/ASA/FWSM/VPN Concentrator Firewall Analyzer supports the following versions of various Cisco devices. Cisco IOS Firewalls: 8xx 18xx 28xx 38xx 72xx 73xx 3005 1900 2911 3925 Cisco FWSM Catalyst Series: Cisco PIX versions: Cisco ASA: Cisco VPN…

Create Your Azure Free Account Today
Advisor Get personalized recommendations and best practices for Azure. Management Governance Unlimited AI Anomaly Detector Detect anomalies in data to quickly identify and troubleshoot issues. AI + Machine Learning 20,000 transactions free tier AI Bot Service Develop intelligent, enterprise-grade bots…
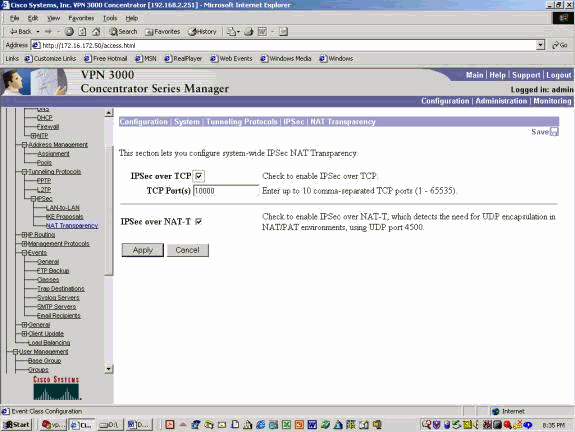
Configuring Multiple VPN Clients to a Cisco VPN 3000 Concentrator Using NAT-Traversal
This document shows how to configure a Network Address Translation Traversal (NAT-T) between Cisco VPN Clients located behind a Port Address Translation (PAT)/NAT device and a remote Cisco VPN Concentrator. NAT-T can be used between VPN Clients and a VPN…

ShoreTel 5300 VPN Concentrator (60032)
Quick View {"id":331061198878,"title":"ShoreTel 4500 VPN Concentrator (60029)","handle":"shoretel-vpn-concentrator-4500","description":"\u003ch2\u003eShoreTel VPN Concentrator 4500 \u003c\/h2\u003e \u003cp\u003eThe ShoreTel VPN Concentrator 4500 supports a wide range of features such as support for up to 10 concurrent VPN tunnels, four RJ-45 ports, and one DB9 Serial Port.…

What is a VPN Concentrator in Japan and Why do You Need It in 2022?
Remote working has become a new normal due to the COVID-19 pandemic. However, this transition is not safe because cyber threats have already migrated from our workplaces to our homes at an alarming rate. Therefore, we are bound to…
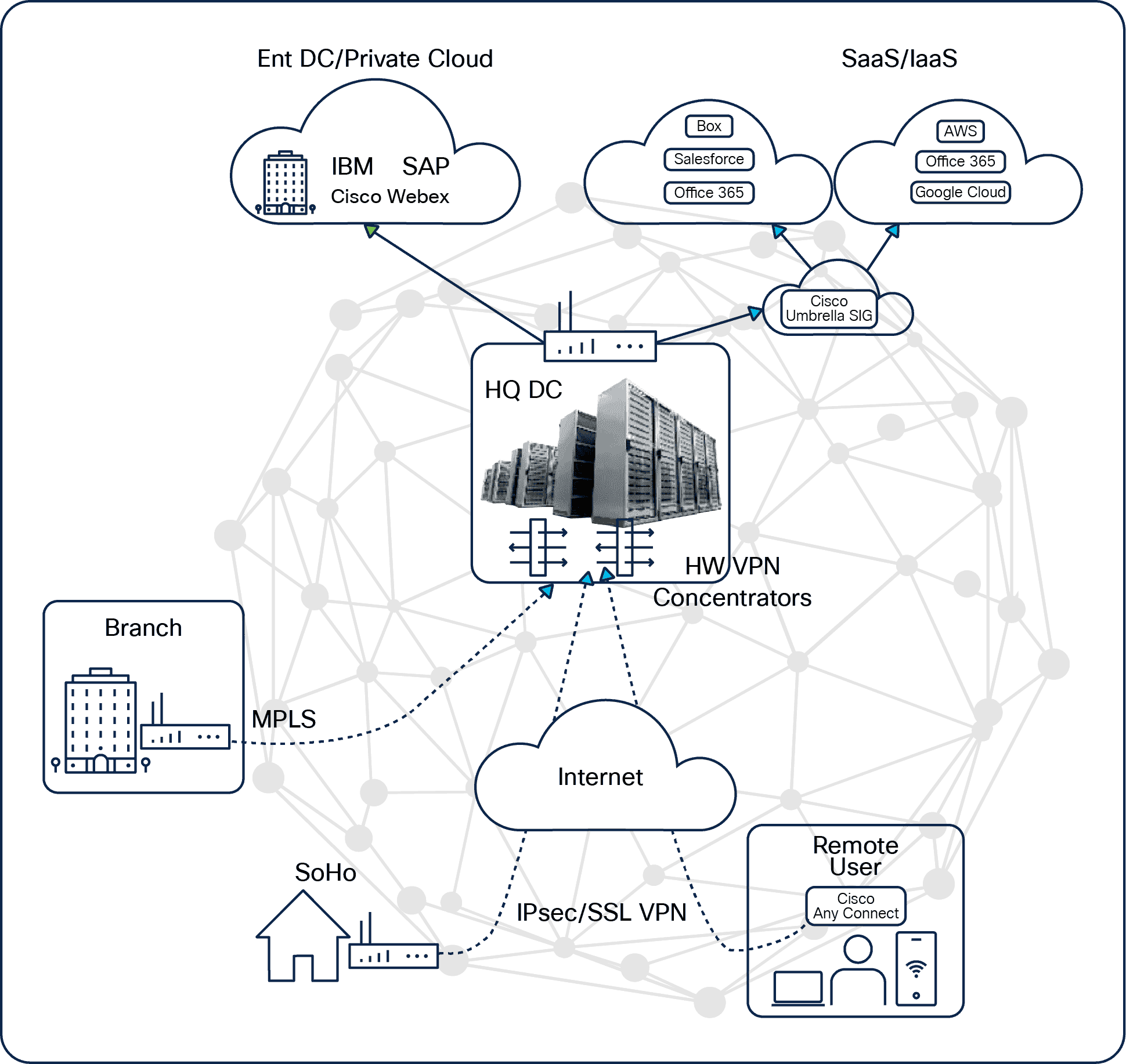
SD-WAN Solution
Redefine the remote-access network with Catalyst SD-WAN Remote Access. Background Remote work has been around for many years, but it has gathered momentum in recent years, driven largely by the pandemic. COVID-19 has introduced a host of changes, including…

VPN Concentrators
What A Virtual- Private Network Concentrator Is As the Coronavirus continues, and no clear certainty as too when businesses will open back up again, employees will still be continuing to work from home. Of course, the security issues that surround…
![[no-title]](https://www.eratool.com/images/ndnav/default-thumb.png)
[no-title]
%PDF-1.3 % 180 0 obj << /Linearized 1 /O 182 /H [ 947 745 ] /L 265678 /E 31174 /N 18 /T 261959 >> endobj xref 180 26 0000000016 00000 n 0000000871 00000 n 0000001692 00000 n 0000001959 00000 n…

The best VPN services of 2024: Expert tested and reviewed
Virtual private networks (VPNs) encrypt your data and hide your IP address. By providing a layer of encryption, VPNs keep your data secure and prevent others from spying on your online activities.A VPN is particularly important when traveling or when you have…

VPN Ultimate
Bahasa Indonesia, Bahasa Melayu, Deutsch, English, English (United States), Filipino, Français, Kiswahili, Nederlands, Norsk, Tiếng Việt, Türkçe, català, dansk, eesti, español, hrvatski, italiano, latviešu, lietuvių, magyar, polski, português (Portugal), română, slovenský, slovenščina, suomi, svenska, čeština, Ελληνικά, Српски, български, русский, עברית,…
