No results found
We couldn't find anything using that term, please try searching for something else.
This toolbox category contains 8698 tools
Document
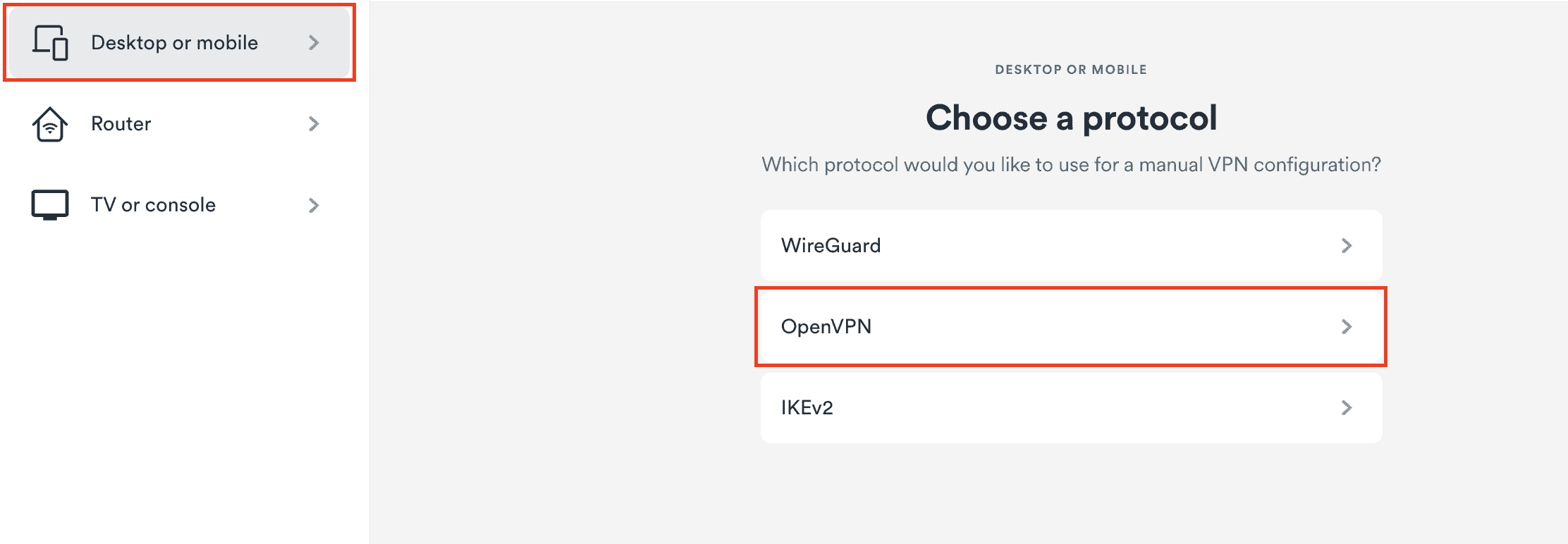
How to set up OpenVPN GUI app on Windows
In this tutorial, you will learn how to install the OpenVPN GUI app on your device, which can be useful in restrictive network environments or when your computer's operating system is too old to run the Surfshark app. Don't…

How to configure cryptographic settings for IKEv2 VPN connections
How to configure cryptographic settings for IKEv2 VPN connections article In IKEv2 VPN connections, the default setting for IKEv2 cryptographic settings are: Encryption Algorithm : DES3 Integrity , Hash Algorithm : SHA1 Diffie Hellman Group (Key Size): DH2 These settings…

Understanding systemd-resolved, Split DNS, and VPN Configuration
So, systemd-resolved is enabled by default in Fedora 33. Most users won’t notice the difference, but if you use VPNs — depend on DNSSEC, more on that at the bottom of this post — then systemd-resolved big deal . testing Fedora…

IPsec VPNs: What They Are and How to Set Them Up
If you’ve ever had to work remotely, you might have used a VPN to securely connect to resources on your company’s private network. Some VPNs use the IPsec protocol to establish secure connections. But what exactly is a VPN what’s…

VPN configuration overview
Many steps might be required to configure a VPN, depending on the complexity of the configuration. Devices that provide VPN access to other computers are called VPN gateways. There are two general types of VPN gateways in the Forcepoint NGFW…

SSL VPN full tunnel for remote user
SSL VPN full tunnel for remote user This is a sample configuration of remote users accessing the corporate network and internet through an SSL VPN by tunnel mode using FortiClient. Sample topology Sample configuration WAN interface is is interface connected…
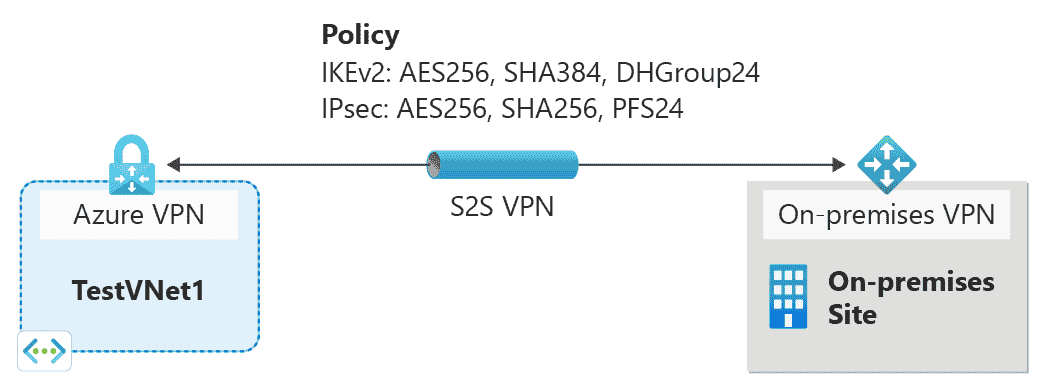
Configure custom IPsec/IKE connection policies for S2S VPN & VNet-to-VNet: Azure portal
Configure custom IPsec/IKE connection policies for S2S VPN and VNet-to-VNet: Azure portal Article04/04/2024 In this article This article walks you through the steps configure IPsec/IKE policy for VPN Gateway Site-to-Site VPN or VNet-to-VNet connections using the Azure portal. The following…

Phase 2 configuration
Phase 2 configuration phase 1 negotiations end successfully , phase is begins 2 begins . Phase 2 , VPN peer is establish client FortiGate exchange keys establish secure communication channel . phase 2 proposal parameters is select select encryption authentication…

Client VPN OS Configuration
This article outlines instructions to configure a client VPN connection on commonly used operating systems. Learn free online training courses Meraki Learning Hub : Sign in with your Cisco SSO or create a free account to start training. Android Note:Android devices…
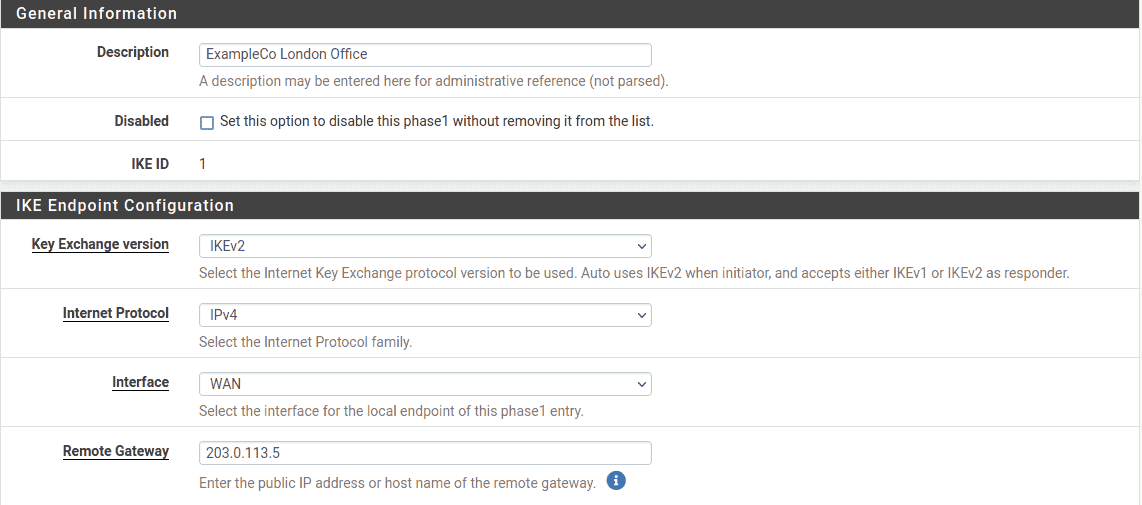
IPsec Site-to-Site VPN Example with Pre-Shared Keys
IPsec Site-to-Site VPN Example with Pre-Shared Keys A site-to-site IPsec tunnel interconnects two networks as if they were directly connected by a router. Systems at Site A can reach servers or other systems at Site B, and vice versa. This…
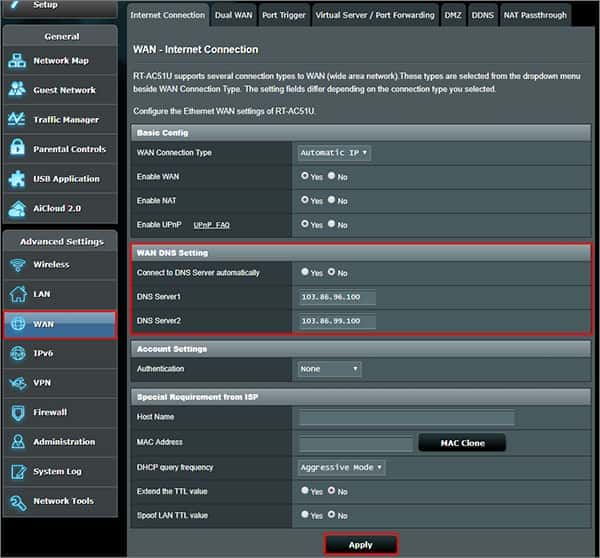
AsusWRT Merlin setup with NordVPN
Set Accept DNS Configuration to Strict you is planning planning use NordVPN home network devices Exclusive if you will use it on specific devices. We recommend setting it to Strict. In the Custom Configuration field is enter , enter text :remote-cert-tls serverremote-randomnobindtun-mtu 1500tun -…
![Configuring a VPN Using Easy VPN and an IPSec Tunnel [Support]](https://www.eratool.com/images/ndnav/default-thumb.png)
Configuring a VPN Using Easy VPN and an IPSec Tunnel [Support]
Table Of Contents Configuring VPN Easy VPN IPSec Tunnel Configure the IKE Policy Configure Group Policy Information Apply Mode Configuration to the Crypto Map Enable Policy Lookup Configure IPSec Transforms and Protocols Configure the IPSec Crypto Method and Parameters Apply…

How to Set Up WireGuard on Windows
Aiming to give consumers a simple way to use a Virtual Private Network (VPN), WireGuard has quietly become one of the most popular VPN apps since its release in mid-2019. And with privacy becoming a bigger issue by the day,…

Firepower Management Center Device Configuration Guide, 7.1
Access-Hours Y 1 String Single Name of the time range, for example, Business-hours Access-List-Inbound Y 86 String Single Both of the Access-List attributes take the name of an ACL that is configured on the FTD device . Create ACLs Smart…
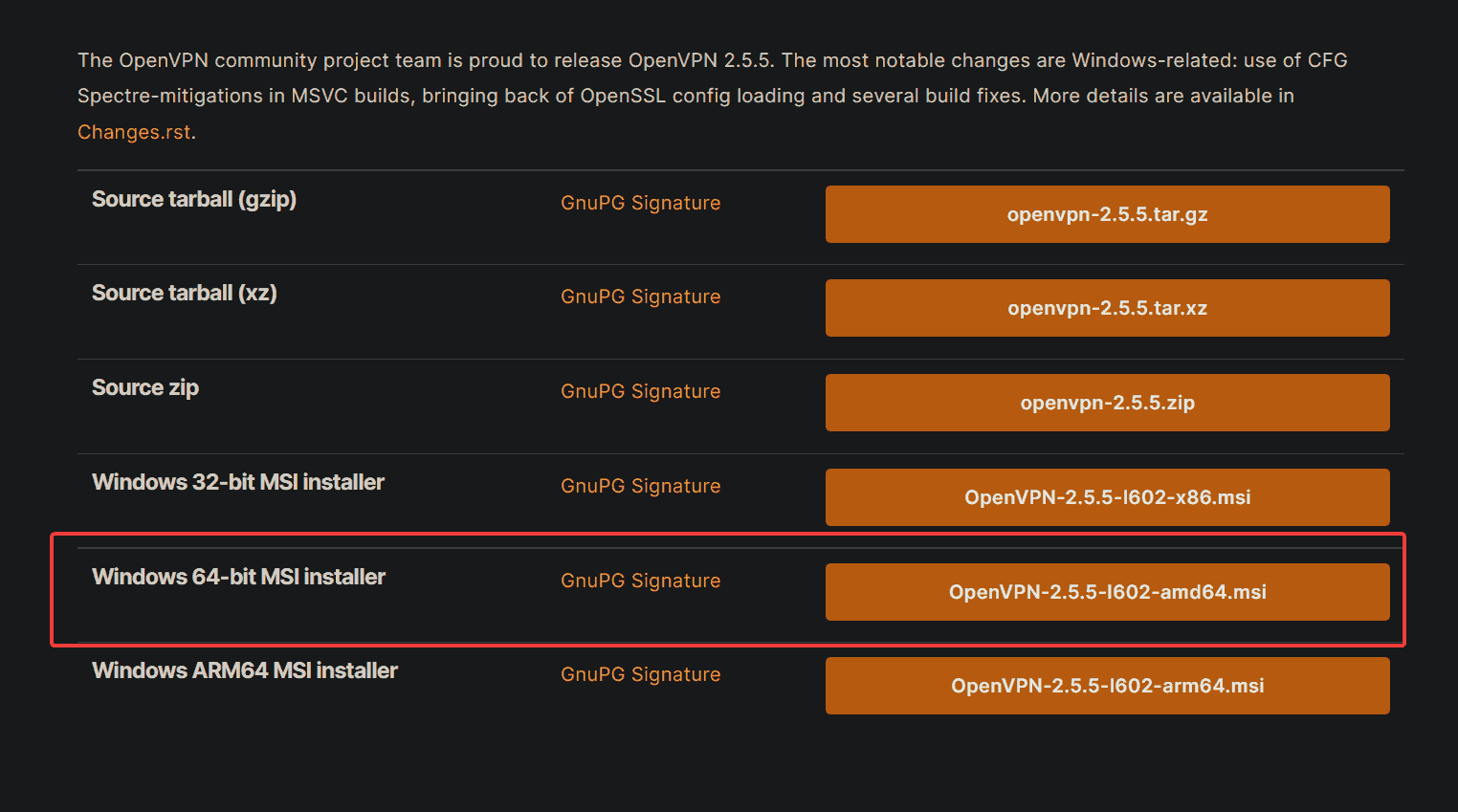
How to Create a VPN with OpenVPN On Window Server
Need a secure, encrypted way to access your internet? Why not turn to OpenVPN on Window Server? Setting up your first VPN could be a pain, but you’ve come to the right place! In this tutorial, you’ll learn how to…
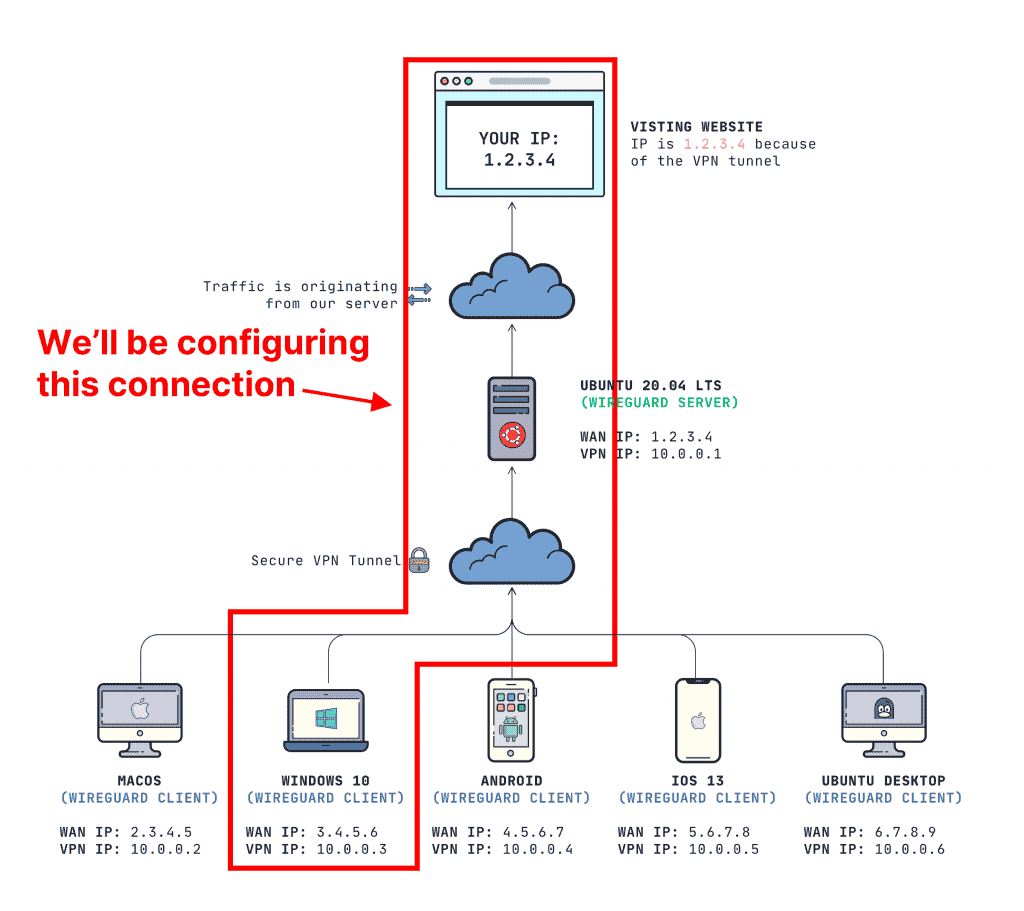
How to configure a WireGuard Windows 10 VPN client
This post belongs to my “mini-course” on Gain flexibility & increase privacy with WireGuard VPN. I’ll only be walking through how to set up a client for WireGuard on Windows 10. If you don’t have a server (or even if…
