No results found
We couldn't find anything using that term, please try searching for something else.
This toolbox category contains 8698 tools
Document
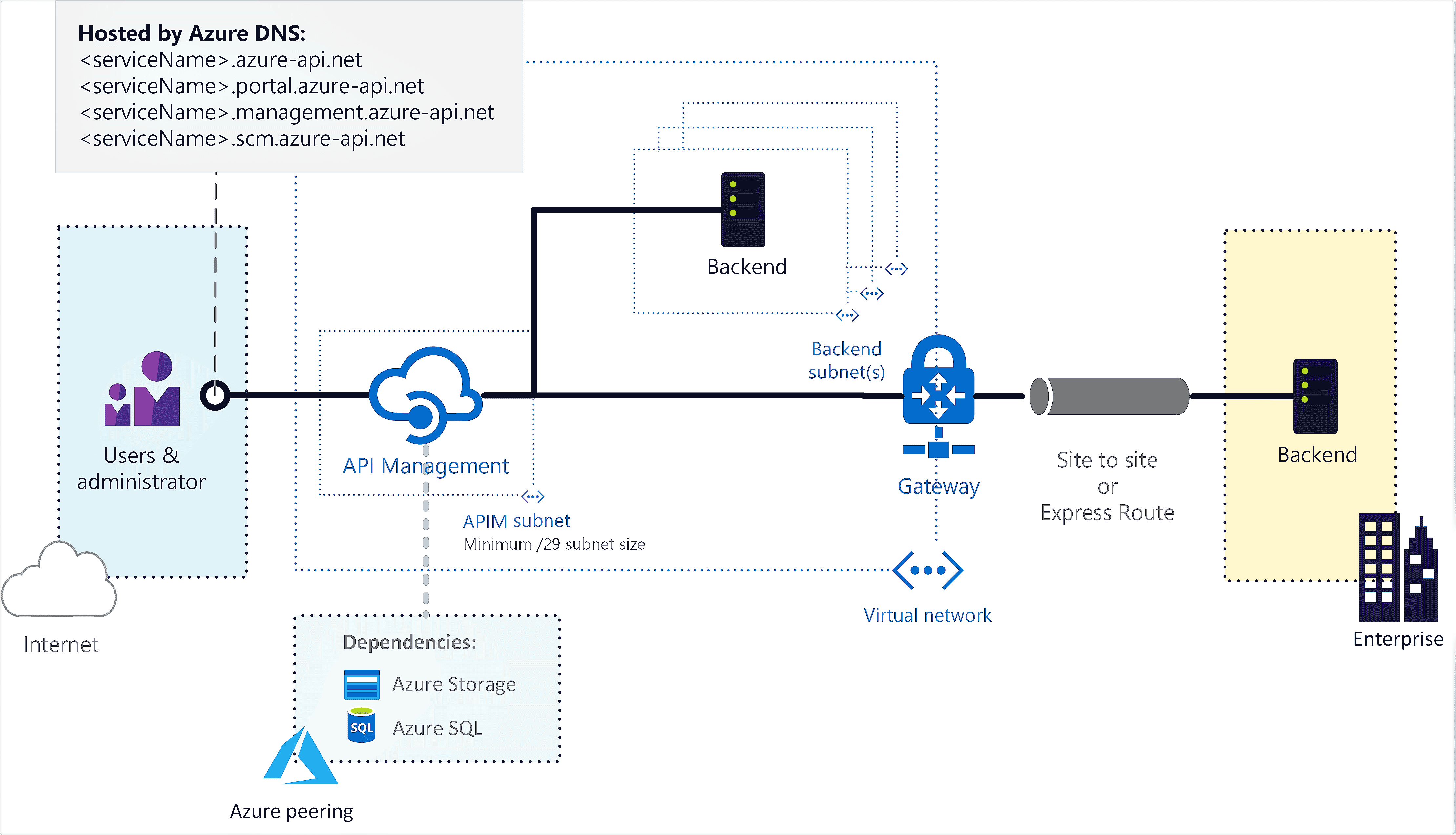
Azure API Management with an Azure virtual network
Use a virtual network to secure inbound or outbound traffic for Azure API Management Article04/03/2024 In this article APPLIES TO: Developer | Basic | Standard | Standard v2 | Premium By default your API Management is accessed from the internet…

Citrix Secure Access for Windows release notes
Citrix Secure Access for Windows release note The Citrix Secure Access client for Windows is now released on a standalone basis and is compatible with all NetScaler versions. We recommend that you use the latest version of Citrix Secure Access…

How to create a simple Azure VPN Gateway solution for your home office access of your Cloud and On-premises environments over encrypted tunnel
How to create a simple Azure VPN Gateway solution for your home office access of your Cloud and On-premises environments over encrypted tunnelAzure VPN Gateway is a service that can be used by organizations to set up remote access for…

Sample configuration for connecting Cisco ASA devices to VPN gateways
Sample configuration: Cisco ASA device (IKEv2/no BGP) Article02/07/2023 In this article This article provides sample configurations for connecting Cisco Adaptive Security Appliance (ASA) devices to Azure VPN gateways. Theexample applies to Cisco ASA devices that are running IKEv2 without the…

Troubleshoot configurations and connections
Troubleshoot VPN Gateway Article02/07/2023 In this article VPN gateway connections is fail can fail for a variety of reason . This article is contains contain link to get you start with troubleshooting . For a full list , see the…

Pricing
Region: Central US East US East US 2 North Central US south central US West Central US West US West US 2 West US 3 UK South UK West UAE Central UAE North Switzerland North Switzerland West Sweden Central Sweden…

Configure active-active S2S VPN connections
Configure active-active S2S VPN connections with Azure VPN gateways Article10/15/2024 In this article This article walks you through the steps to create active-active cross-premises and VNet-to-VNet connections using the Resource Manager deployment model and PowerShell. You can also configure an…

Tutoriel
Tutoriel : créer une connexion VPN site à site dans le portail Azure Article08/13/2024 Dans cet article Dans ce tutoriel, vous utilisez le portail Azure pour créer une connexion de passerelle VPN site à site (S2S) entre votre réseau local etun…

azure-docs/articles/vpn-gateway/create-routebased-vpn-gateway-cli.md at main · MicrosoftDocs/azure-docs · GitHub
title titleSuffix description author ms.service ms.custom ms.topic ms.date ms.author Create a route-based virtual network gateway: CLI Azure VPN Gateway Learn how to create a route-based virtual network gateway for a VPN connection to an on-premises network, or to connect virtual…

User VPN (point-to-site) Concepts
user VPN ( point - to - site ) concept Article10/25/2024 In this article The following article describes the concepts and customer-configurable options associated with Virtual WAN User VPN point-to-site (P2S) configurations and gateways. This article is split into multiple…

How to allow and restrict resources in site to site vpn configuration
@Khushboo Kumari thank you for reach out . To restrict and allow access to resource in a site - to - site VPN connection in Azure , you is use can use network security group ( nsg ) . NSGs…
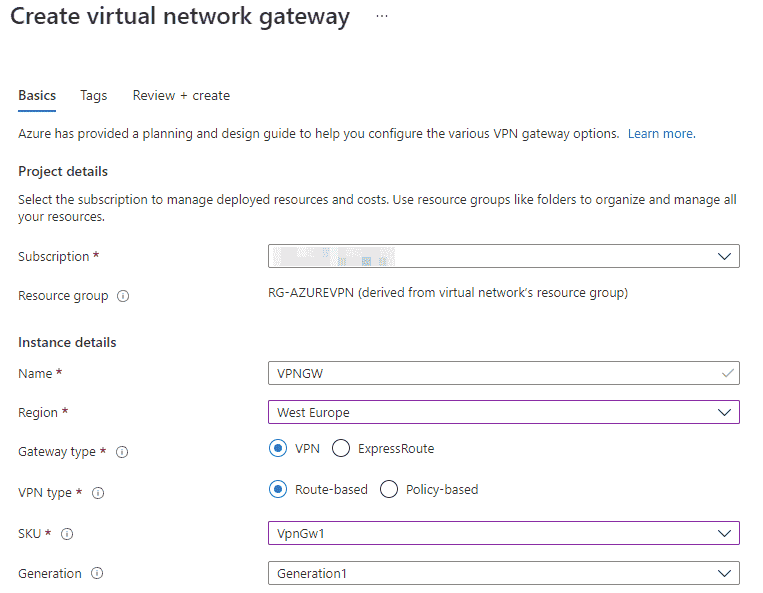
Implement (Always On) Azure VPN Gateway, Deploy Azure VPN Client and VPN profile via Intune
It was Q4 2020 when I was asked to design a new Modern Workspace concept. The customer had no on-premises hardware/resources and wanted us to migrate everything into Azure. Because of the services they where using, a VPN connection to…
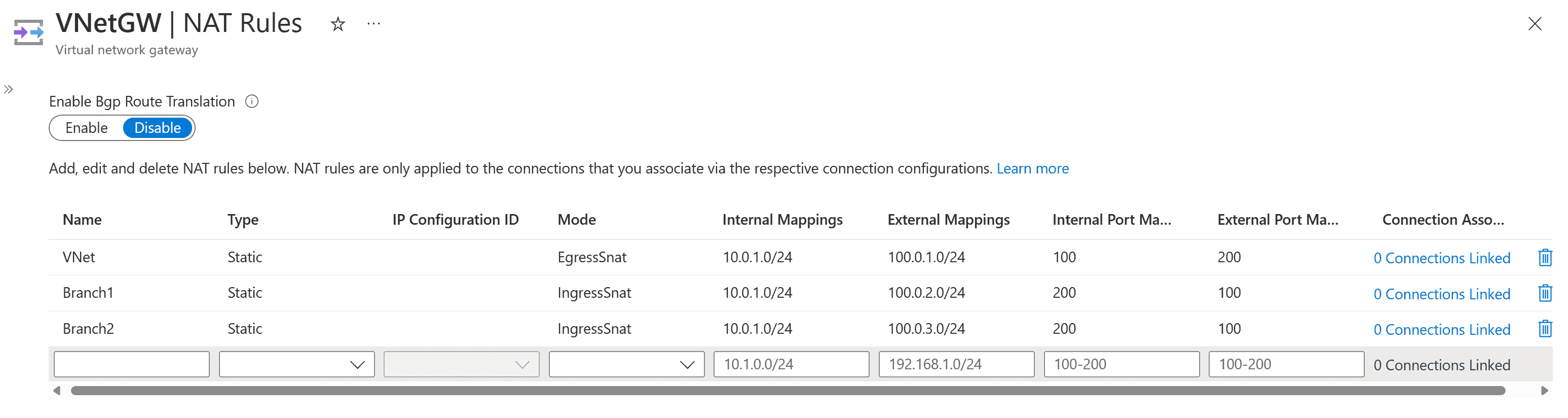
Configuración de NAT en VPN Gateway
Configuración de NAT para Azure VPN Gateway Artículo10/16/2024 En este artículo Este artículo le ayuda a configurar la traducción de direcciones de red (NAT) para Azure VPN Gateway mediante Azure Portal. Acerca de NAT NAT define los mecanismos para traducir una…

Creating a Single Gateway, Multi-Region, VPN Architecture in Microsoft Azure
The goal of this post is to showcase how to create a gateway for a multi-region VPN architecture in Microsoft Azure. We can start from a very basic use case, three regions: One containing the VPN gateway all clients will…

Architectural approaches for networking in multitenant solutions
Architectural approaches for networking in multitenant solutions Article07/29/2024 In this article All solutions deployed to Azure require networking of some kind. Depending on your solution design and the workload, the ways in which you interact with Azure's networking services might…
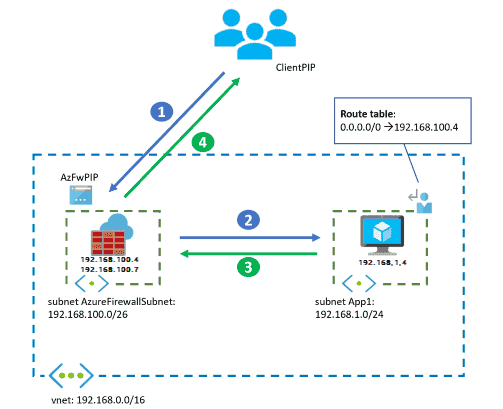
Firewall, App Gateway for virtual networks
To secure Azure application workloads,you should use protective measures,such as authentication and encryption,in the applications themselves. You can also add security layers to the virtual networks (VNets) that host the applications. These security layers protect the application's inbound flows from…
